The blockchain has tremendous potential for fraud prevention and cyber security. With this series of articles, we will explore how the blockchain will change the cyber risk game. Jérôme Kehrli
In my first article, I have introduced the blockchain concept, presents what it is in the light of its initial deployment in the Bitcoin project, key problems solved by blockchain, and the blockchain operation principle.
With this second part, we dig into the technical aspects to complete our thorough introduction to blockchain. Concrete business applications and evolutions will be discussed in an article to follow in the coming weeks.
1. Technical aspects of a blockchain
In the Bitcoin system, a blockchain is a transaction database shared by all nodes participating in a system based on the Bitcoin protocol.
A full copy of a currency's block chain contains every transaction ever executed in the currency. With this information, one can find out how much value belonged to each address at any point in history.
1.1 The blockchain data structure
The blockchain data structure is an ordered, back-linked list of blocks of transactions. Every block contains a hash of the previous block. This has the effect of creating a chain of blocks from the genesis block to the current block. Each block is guaranteed to come after the previous block chronologically because the previous block's hash would otherwise not be known. Each block is also computationally impractical to modify once it has been in the chain for a while because every block after it would also have to be regenerated.

Transaction data is permanently recorded in these blocks as if they were files. These blocks can be thought of as the individual pages of a city recorder's recordbook (where changes to title to real estate are recorded) or a stock transaction ledger. Over time, blocks are organized into a linear sequence, also known as a blockchain.
New transactions are constantly being processed by miners into new blocks, which are then added to the end of the chain and can never be changed
or removed once accepted by the network.
1.2 A first view on a block structure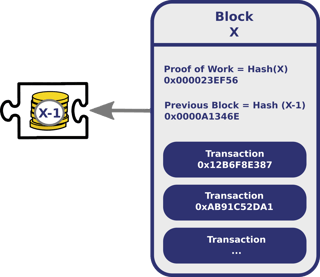
Each block contains, among other things, arecord of some or all recent transactions, as well as a reference to the block that came immediately before it. It also contains an answer to a difficult-to-solve mathematical puzzle known as the hash or proof of work—more on that later!
1.3 A miner's life
In the Bitcoin world, transactions are broadcast to the network by the sender, and all peers trying to solve blocks collect the transaction records and add them to the block they are working to solve. This is called mining.
Mining is the process of adding transaction records to Bitcoin's public ledger of past transactions. This ledger of past transactions is called the blockchain because, simply, it is a chain of blocks. The blockchain serves to confirm to the rest of the network that the transactions have taken place. Bitcoin nodes use the block chain to distinguish legitimate Bitcoin transactions from attempts to re-spend bitcoins that have already been spent elsewhere.
Mining is intentionally designed to be resource-intensive and difficult so that the number of blocks found each day by miners remains steady. Individual blocks must contain a proof-of-work to be considered valid. This proof of work is verified by other Bitcoin nodes each time they receive a block. Bitcoin uses the hashcash proof-of-work function.
The primary purpose of mining is to allow Bitcoin nodes to reach a secure, tamper-resistant consensus.
The algorithm
Mining a block is difficult because the SHA-256 hash of a block's header must be lower than or equal to the target in order for the block to be accepted by the network.
Let’s simplify this problem for explanation purposes: The hash of a block must start with a certain number of zeros. The probability of calculating a hash that starts with many zeros is very low, therefore many attempts must be made. In order to generate a new hash each round, a nonce is incremented.
Miners implement the following (simplified) algorithm:

1.4 Difficulty adjustment
The difficulty is the measure of how difficult it is to find a new block compared to the easiest it can ever be. It is recalculated every 2016 blocks to a value such that the previous 2016 blocks would have been generated in exactly two weeks had everyone been mining at this difficulty. This will yield, on average, one block every 10 minutes.
As more miners join, the rate of block creation will go up. As the rate of block generation goes up, the difficulty rises to compensate so that the rate of block creation is pushed back down.
Any blocks released by malicious miners that do not meet the required difficulty target will simply be rejected by everyone on the network and thus will be worthless.

Again, the difficulty of the mathematical problem is automatically adjusted by the network, such that it targets a goal of solving an average of six blocks per hour. The network comes to a consensus and automatically increases (or decreases) the difficulty of generating blocks.
1.5 Miner retribution (and Bitcoin creation)
Mining is also the mechanism used to introduce bitcoins into the system. Miners are paid transaction fees as well as a subsidy of newly created coins. This both serves the purpose of disseminating new coins in a decentralized manner as well as motivating people to provide security for the system. In other words, the subsidy provides incentive for miners to put their computation power at the disposal of the blockchain network.
Because there is a reward of brand new bitcoins for solving each block, every block also contains a record of which Bitcoin addresses or scripts are entitled to receive the reward. This record is known as a generation transaction (or a coinbase transaction) and is always the first transaction appearing in every block.
The number of bitcoins generated per block starts at 50 and is halved every 210,000 blocks (about four years).

In addition to the generation transaction, miners are motivated to include transactions in their blocks because of attached transaction fees. A modest fee is received for every transaction in the newly mined block.
1.6 Bitcoin supply limits
In the specific case of the Bitcoin, Satoshi had the idea of limiting the bitcoin supply early on. Of course, there is an important reason behind this.
In a centralized economy, currency is issued by a central bank at a rate that is supposed to match the rate of goodsexchanged, so that these goods can be traded with stable prices. The monetary base is controlled by a central bank. In the United States, the Fed increases the monetary base by issuing currency, increasing the amount banks have on reserve, and, more recently, printing money electronically in a process called Quantitative Easing.
In a fully decentralized monetary system, there is no central authority that regulates the monetary base. Instead, currency is created by the nodes of a peer-to-peer network. The Bitcoin generation algorithm defines, in advance, how currency will be created and at what rate. Any currency that is generated by a malicious user that does not follow the rules will be rejected by the network and thus is worthless.
Bitcoins are created each time a user discovers a new block. As a reminder, the rate of block creation is adjusted every 2016 blocks to aim for a constant two week adjustment period (equivalent to 6 per hour.) The number of bitcoins generated per block is set to decrease geometrically, with a 50% reduction every 210,000 blocks, or approximately four years. As a result, the number of bitcoins in existence is not expected to exceed 21 million.
But why 21 million? Some speculate that 21 million matches a 4-year reward halving schedule; or that the ultimate total number of Satoshis that will be mined is close to the maximum capacity of a 64-bit floating point number. Satoshi has never really justified or explained many of these constants.
The formula is the following:

This decreasing-supply algorithm was chosen because it approximates the rate at which commodities like gold are mined. Users who use their computers to perform calculations to try and discover a block are therefore called Miners.

1.7 Wallet cryptography
A wallet is basically the Bitcoin equivalent of a bank account. It allows you to receive bitcoins, store them, and then send them to others.
But the term "Bitcoin wallet" is a bit of a misnomer. Bitcoin wallets don't hold actual bitcoins because bitcoins are actually stored on the blockchain. Instead, Bitcoin wallets hold the private keys that give users the right to use those Bitcoins. Each Bitcoin wallet comes with at least two keys – one public, and one private – and multisig wallets can have more.
The public key lets any Bitcoin user send a sum of bitcoins directly to any other Bitcoin user, without a middle man. The private key must be kept as secure as possible, since anyone who gets a hold of it has access to every bitcoin associated with it.
There are several types of wallets out there: Software wallets, web wallets, and paper/cold wallets. There is also a relationship between wallet and Bitcoin addresses.
Bitcoin address
A Bitcoin address, or simply address, is an identifier of 26-35 alphanumeric characters, beginning with the number 1 or 3, which represents a possible destination for a Bitcoin payment. Addresses can be generated at no cost by any user of Bitcoin.
There are currently two address formats in common use:
- Common P2PKH which begin with the number 1, eg: 1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2.
- Newer P2SH type starting with the number 3, eg: 3J98t1WpEZ73CNmQviecrnyiWrnqRhWNLy.
A Bitcoin address is a single-use token. Like e-mail addresses, you can send bitcoins to a person by sending them to one of that person’s addresses. However, unlike e-mail addresses, people have many different Bitcoin addresses and a unique address should be used for each transaction.
A Bitcoin address is a 160-bit hash of the public portion of a public/private ECDSA keypair. Using public-key cryptography, you can sign data virtually with your private key and anyone who knows your public key can verify that the signature is valid.

The private key aims at enabling solely and only the owner of an address to create a transaction where the sender of the bitcoin is that owner. Keeping this private key secret is of utmost importance. If someone steals that private key from a wallet owner, he can drag all its money out by creating transaction from that wallet to his own wallet in a perfectly legitimate way.
It's impossible for an attacker to forge a fraudulent transaction from someone else's wallet without having that very private key. On the other hand, every miner, every network member can safely and rapidly ensure the validity of the transactions in a block by using the public key of the corresponding wallet owners.
1.8 Merkle trees
A Merkle tree constructed by hashing paired data (the leaves), then pairing and hashing the results until a single hash remains like a virtual root. The Merkle tree is constructed such that if any single leaf transaction is changed, all hashes along the branch would be changed and ultimately the merkle root as well. This is a key property ensuring security of the blockchain.
Merkle trees in Bitcoin use a double SHA-256, the SHA-256 hash of the SHA-256 hash of something.
If, when forming a row in the tree (other than the root of the tree), it would have an odd number of elements, the final double-hash is duplicated to ensure that the row has an even number of hashes.
First, form the bottom row of the tree with the ordered double-SHA-256 hashes of the byte streams of the transactions in the block. Then the row above it consists of half that number of hashes. Each entry is the double-SHA-256 of the 64-byte concatenation of the corresponding two hashes below it in the tree.
This procedure repeats recursively until we reach a row consisting of just a single double-hash. This is the Merkle root of the tree.

In the blockchain, Merkle trees enable the verification of a transaction in a much faster way than validating a transaction by recomputing the hash from the whole block data. In addition, as new transactions are broadcast to the network, updating the Merkle root takes only log(n) hash operations on small data instead of re-hashing everything.
1.9 Peer to peer network

A blockchain is a ledger of facts, replicated across several computers assembled in a peer-to-peer network that operates on a cryptographic protocol. In the case of bitcoins, users send units of currency, by broadcasting digitally signed messages to the network using Bitcoin wallet software. In the case of more advanced and recent blockchain technologies - called blockchain 2.0 (such as Ethereum), users broadcast Smart Contracts, events, or API calls on these Smart Contracts.
Members of the network are anonymous individuals called nodes or miners since initially almost all of them were running the mining algorithm presented above.
Both new transactions and newly-mined blocks are broadcasted to the peer-to-peer network.
1.10 Orphaned, Extinct and Staled Blocks
Because each block contains a reference to the prior block, the collection of all blocks in existence can be said to form a chain. However, it's possible for the chain to have temporary splits, for example, if two miners arrive at two different valid solutions for the same block at the same time, unbeknownst to one another.
The peer-to-peer network is designed to resolve these splits within a short period of time, so that only one branch of the chain survives.
The client accepts the longest chain of blocks as valid. The length of the entire block chain refers to the chain with the most combined difficulty, not the one with the most blocks. This prevents someone from forking the chain and creating a large number of low-difficulty blocks, and having it accepted by the network as longest.

2. Blockchain 2.0
The Blockchain 2.0 is an evolution of the blockchain protocol that enables coding and programming in the form of Smart Contracts as well as exchange transactions.
This means developers are now able to build programs and API's on the Blockchain Protocol. Moreover, this relatively new concept involves the development of programs that can be entrusted with money.
Smart contracts are programs that encode certain conditions and outcomes. For instance, when a transaction between two parties occurs, the program can verify if the product/service has been sent by the supplier. Only after verification is the sum transmitted to the suppliers account.
By developing ready-to-use programs that function on predetermined conditions between the supplier and the client, smart programs ensure a secure escrow service in real time at near zero marginal cost.
Apart from Financial transactions, smart contracts are now entering a number of different industries. For instance in the legal system, companies like Empowered Law use the public distributed ledger of transactions that makes up blockchains to provide Multi-Signature account services for asset protection, estate planning, dispute resolution, leasing and corporate governance.
Ethereum
Ethereum intends to bring together both a crypto ledger and a Turing-complete programming language, which is a language can be used to write actual computer programs. They intend to make a browser that is the Swiss-army knife of blockchain and encryption tools, allowing non-technical users to truly leverage the web.
Ethereum aims to implement a globally decentralized, un-ownable, digital computer for executing peer-to-peer contracts. Put more simply, Ethereum is a world computer that you can't shut down.

The Blockchain 2.0, its opportunities, as well as its limitations will be the topic of a dedicated article expected in the coming weeks on this very blog.
3. Summary
In summary, these are the key aspects of the blockchain technology:

A blockchain is an amazing technology. I strongly believe it has the potential to revolutionize a whole lot of different industries. In fact, this revolution will be the topic of my third blockchain article on this blog that should appear in the near future. Stay tuned!




