Our software helps banks and telcos detect fraudulent activity related to mobile wallets and ATMs, and has even helped catch the fraudsters red-handed, writes Bernard Rono
Mobile wallet fraud is found wherever mobile wallet services are popular. This is a particular problem in Africa, not just for the banks and telcos operating them but for society as a whole.
In June this year, Interpol warned: “There are strong indications that mobile money-enabled criminality represents a significant threat to society in Africa.” The international police agency is concerned that criminal gangs and terrorist organizations are netting enormous sums through fraud to fund their activities. Clearly, more needs to be done to stop it.
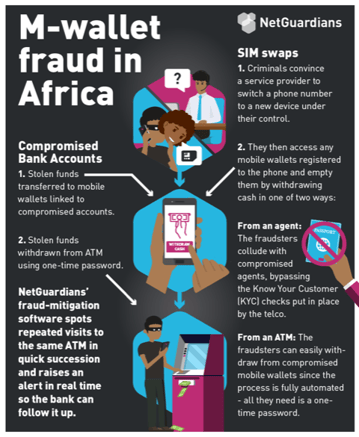
There are two main ways fraudsters get their hands on stolen cash using mobile wallets: SIM swaps that give them access to the wallet, and bank fraud, whereby the wallet is used to quickly move the proceeds of other criminal activity.
SIM swaps leading to account take-over
SIM swapping is when criminals take over someone’s mobile phone by persuading the service provider to switch the phone number to a new device under their control. The criminals can then access whatever apps the victim has on their phone – social media, email, contacts and bank accounts. It has proved hard to stop and can affect anyone – even tech moguls like Twitter’s CEO Jack Dorsey have been hit.
The ubiquity in Africa of mobile wallet services such as M-Pesa means that nearly everyone has money accessible via a phone. Using a SIM swap, fraudsters can take control of a phone that is almost certain to have a mobile wallet app and empty that wallet. Additionally, many people link their mobile wallets to bank accounts . When that is the case fraudsters can easily access the bank account via a SIM swap too. In South Africa, for example, the authorities saw a threefold increase in mobile fraud in 2018, with the criminals netting more than R262 million in some 23,000 attacks including via mobile wallets.
To get the cash from a mobile wallet fraudsters can either go to a specified agent or withdraw the cash from an ATM. Given that an agent will ask to see an ID card or passport as a security check, the fraudsters avoid this option. When they go to an ATM, the checks are automated and involve codes sent to the mobile phone, which the fraudster already controls.
Clearly, given the rise in this type of fraud, the controls are ineffectual. But banks using NetGuardians’ fraud-mitigation software are better placed. The software picks up on suspicious behavior – for example, repeated trips in quick succession to the same ATM to withdraw cash at or just below the maximum allowed – usually $400 a day. It sends an alert to the bank, which follows up, blocking and investigating access from the ATM to the mobile wallet.
ATMs as conduit for stolen funds
But SIM swaps are only part of the mobile wallet/ATM/fraud problem. Fraudsters are also using mobile wallets to move funds stolen from banks and net far larger sums. They transfer the stolen money to mobile wallets such and then withdraw that money at ATMs, which have automated checks they can circumvent. Again, the fraudsters have proved hard to stop. But just as data analytics can spot SIM-swap fraud, so the algorithms can spot suspicious behavior linked to wider frauds that use ATM and mobile wallet withdrawals and alert the bank investigation team, which then contacts the police.
Caught red handed
In one case that was spotted and stopped by NetGuardians’ software, a corrupt employee at a large bank in Kenya had transferred $500,000 from an internal bank account to an account controlled by fraudsters. This sum was divided up and transferred to a large number of M-Pesa mobile wallets. The fraudsters then requested to withdraw the money from the mobile wallets via ATMs owned and operated by a second, much smaller bank.
The low withdrawal limits again meant the fraudsters had to make multiple requests for each wallet. The amounts were at or just below the threshold, in quick succession, and at times when the ATMs were unlikely to be busy – at night and weekends, particularly on Sunday mornings when many people are at church.
NetGuardians’ software installed by the bank identified these requests as suspicious, noting their timing, frequency and size, and raised an alert in real time. This meant that the bank could check the ATMs’ CCTV, identify the people withdrawing the cash and tell the authorities – who were able to catch the fraudsters in the act, arrest them, recover much of the money, and return it to the original bank.
Monitoring patterns of behavior
NetGuardians’ software uses machine learning and behavioral analytics to look for patterns across all the ATM transactions at a bank. When a pattern includes suspicious activity such as repeated withdrawals by the same person from multiple wallets at or just below the limit from one ATM over a short period of time it raises an alert in real time.
This level of real-time detection is critical to stopping mobile wallet fraud and protecting the millions of people who rely on these services to pay bills, settle up with friends, buy goods and services, as well as to protect the banks. And when it comes to the bigger picture, it also helps protect society from the nefarious activities of organized criminal gangs.